Challenges
As much as I love solving CTF challenges, I also greatly enjoy designing my own puzzles. This page indexes some challenges I have created in the past for various occasions (not an exhaustive list).
SSTIC 2024: The Green Shard Brawl
#pwn #linux #heap
A binary exploitation problem created for the renowned, annual SSTIC challenge. It consists of a Linux client for a multi-player SDL game written in C, and a Python server that implements a custom protocol. The goal is to spawn a reverse shell on another player’s machine solely by interacting with the server.
You can download the challenge files here, including a Docker Compose setup to run both the server and the victim’s client.
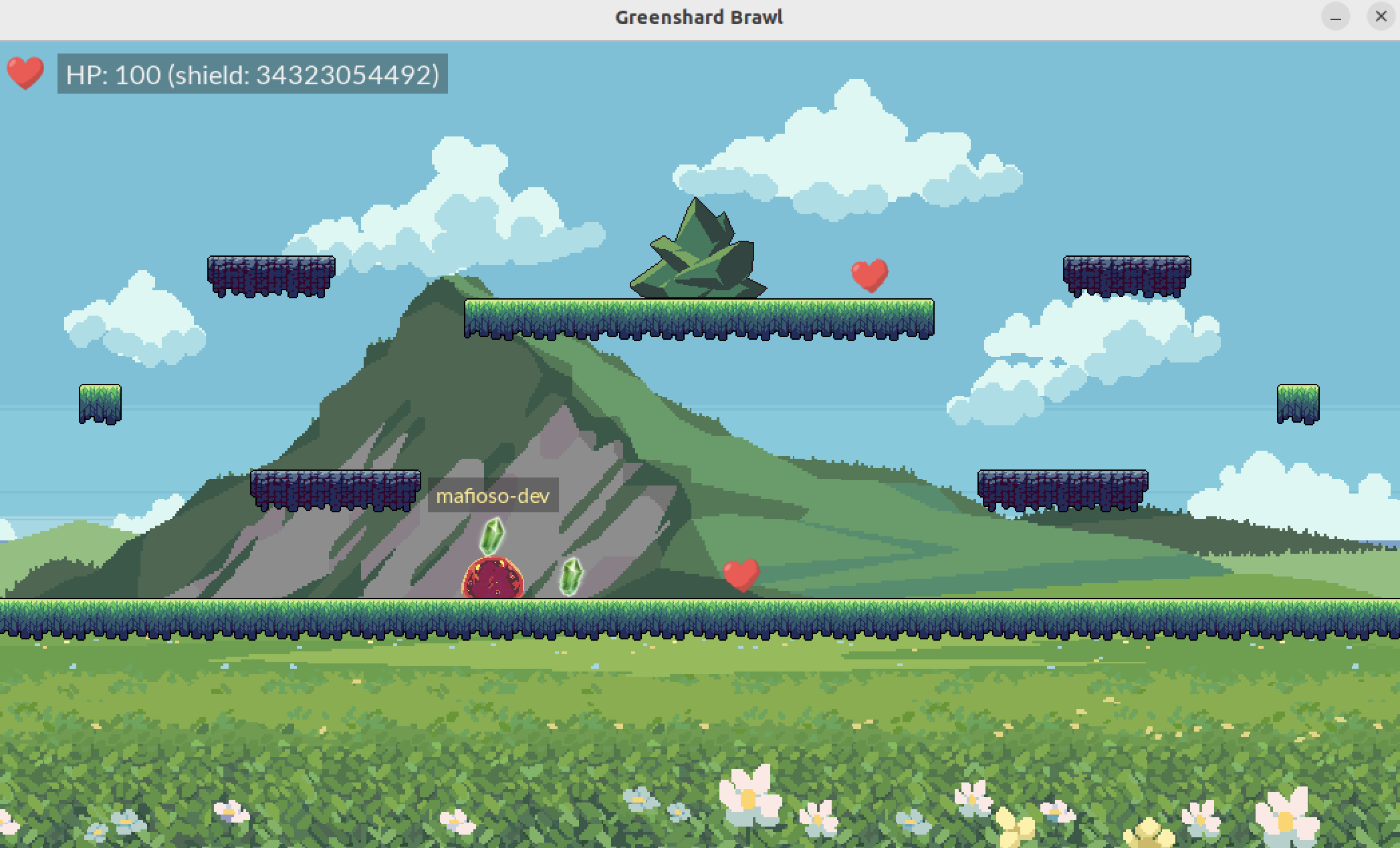
Green Shard Brawl is a fun way to learn about glibc heap exploitation (fastbin, tcache, safe-linking…) in a unique client-to-client exploitation setting. The vulnerabilities are rather easy to spot, which allows to focus primarily on exploitation. The sources for the client are not given, however the binary does contain symbols.
Multiple write-ups about this challenge are featured over on SSTIC’s website.
ECW 2023: kaleidoscope
#reverse #windows #vm
A reverse engineering challenge made for the European Cyber Week CTF qualifiers, focusing on Windows-specific mechanisms and obfuscation, with a little twist.
You can download the challenge here (password: ecw2023).
I published an official, detailed write-up for this challenge over on Thalium’s blog.
ECW 2023: spaceships
#reverse #puzzle
A reverse engineering challenge made for the European Cyber Week CTF qualifiers which consists of a single ELF binary file (download), sheltering an interesting visual puzzle.
Here are some community write-ups for this challenge:
- https://basilics.github.io/2023/10/02/Spaceships.html
- https://github.com/apoirrier/CTFs-writeups/blob/master/ECW2023/Reverse/Spaceships.md
Root-Me 10K CTF (2022): chef’s kiss
#reverse #misc
I came up with this challenge idea for an event organized by Root-Me. It fits into a single URL, which redirects to a CyberChef recipe.
You can find my official write-up for this challenge over here.
ECW 2021: Pipe Dream
#reverse #linux #puzzle
A reverse engineering challenge (download) made for the European Cyber Week CTF qualifiers, that leverages some specific Linux-specific mechanisms to implement a logic puzzle.
I released an official, detailed write-up for this challenge here.